One of the biggest challenges that businesses face today is maintaining collaboration within a remote workforce in response to the COVID-19 pandemic. While remote working allows for better productivity and flexibility, it can be tough to encourage collaboration when people are miles apart.
Blog
Blog
Business Continuity and Disaster Recovery – Part 3 Security Appliances

Welcome back! In part three we will discuss the many facets of network security from firewall appliances to employee training. While a security appliance like a firewall can help keep bad actors from unauthorized access to your network, if improperly configured and implemented, those appliances can act like the landing lights at an airport.
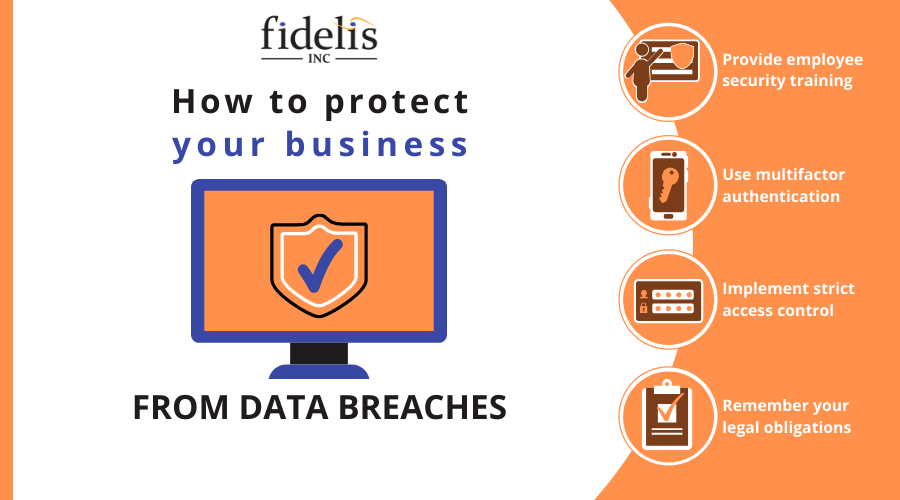
The consequences of data breaches to your business
What is the importance of hardware in cybersecurity?

How often do you think of hardware in relation to your business’s cybersecurity? If you answered “not often,” then you’re not alone; many companies would have the same answer. When it comes to cybersecurity, individuals and organizations typically think about the use of antivirus programs, firewalls, and intrusion prevention systems (IPS). But little do many know that hardware also plays an important role in security.
Phone and Conference Call Etiquette
Avoid these five social media blunders to improve your cybersecurity
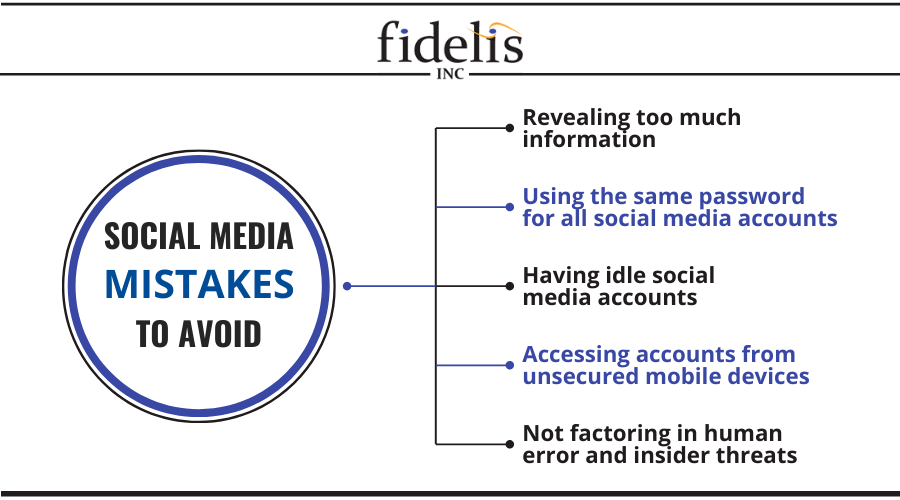
Social media is one of the most critical tools you can leverage to increase your brand awareness. It also lets you interact with your audience on multiple platforms and serve your customers better. Your target audience is most likely part of the 250 million social media users in the United States, so planning a social media strategy should be one of your priorities.
Business Continuity and Disaster Recovery – Part 2 Backup Solutions
Internal vs. external IT: Which is better for SMBs?
Business Continuity and Disaster Recovery – Part 1

The COVID-19 crisis has many businesses scrambling to continue working while following the guidance of our leaders to Stay Home – Stay Safe. During this time, Fidelis has been working diligently setting our clients up with remote network access and getting voice services set up to allow their staff to work remotely.
Guidelines & Tips for Safely Working Remotely

Remote work is surging as a response to the COVID-19 outbreak, but it brings new productivity, security, and communication challenges. For example, if an employee-owned device (laptop, PC, etc.) is connected to the company’s network via a VPN connection and it contains a virus or malware, the malware could spread to your company’s network.